
In today’s era, where data leaks and privacy issues are on an upward trend, it becomes crucial to safeguard important data stored in the Customer Relationship Management (CRM) system. For organizations that are using vTiger CRM, one such method that helps in protecting and masking sensitive customer details is field masking.
Field masking can be described as a very basic but useful technique that enables the users of a system to hide or mask specific fields from reading or viewing in the CRM. This is particularly useful for fields that store highly sensitive data such as PINs, credit cards, social security numbers, or passwords.
In this blog, we’ll start by looking at what field masking is and why it is relevant, we’ll then move to how it is done in vTiger CRM to secure your data further.
What is Field Masking?
Field masking is the method of hiding or obscuring a data within view or usage so that unauthorized personnel are unable to view any information on the field. In layman’s terms, this translates to editing a field in your CRM such that it displays part of a value instead of the entire value (for example, just showing the first 4 digits of a telephone number), or not displaying it at all.
For example:
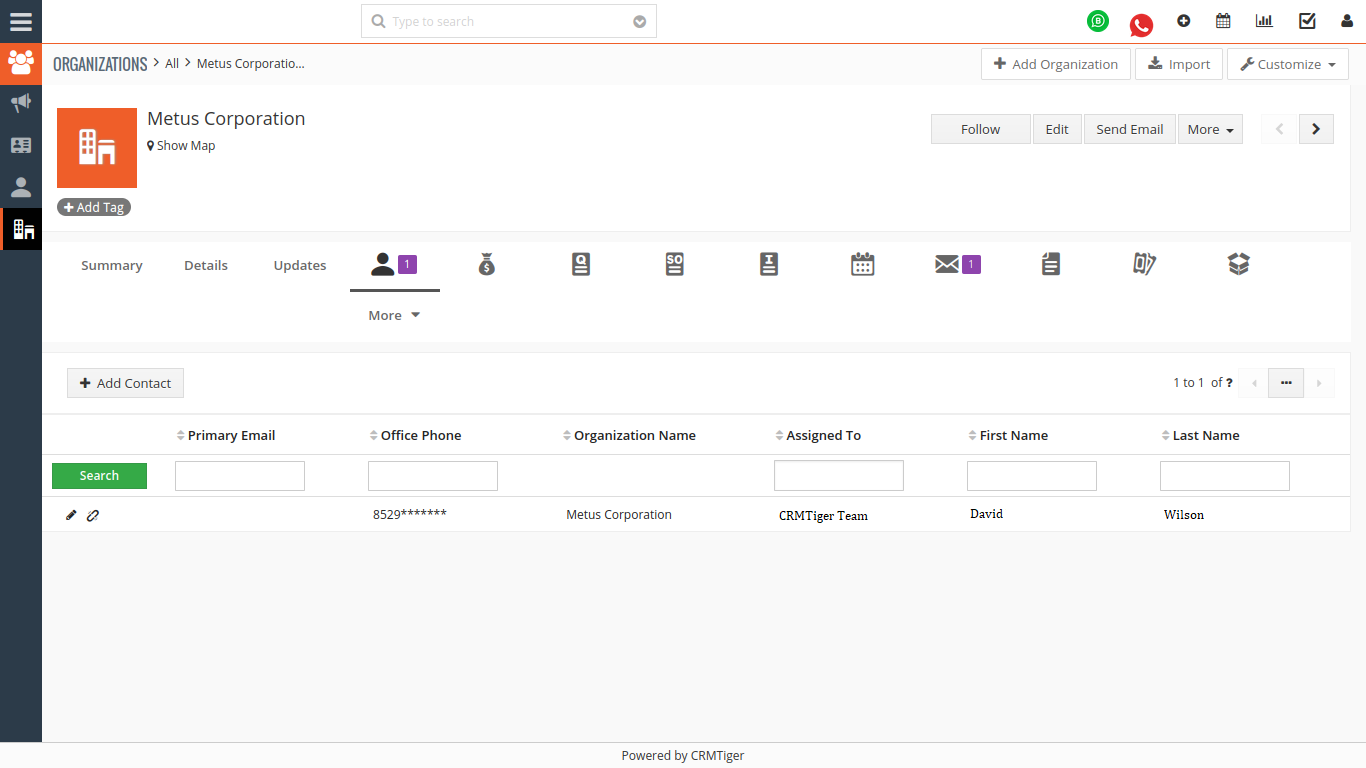
- Phone Number: A phone number could be shown as 9123-****-****, with the last eight digits masked for privacy.
In this way, customer privacy remains preserved and at the same time authorized users can still access the CRM for customer communications or transaction processing within the database.
Why Is Field Masking Important in vTiger CRM?
- Data Protection: Below are the fields in which field masking is effective: In a CRM system, sensitive and highly sensitive data such as personal, financial and health information are likely to be stored. Using field masking helps to conceal sensitive data that should not be visible, reducing the risk of breaching an organization’s data.
- User Access Control: As different users are represented in a CRM system their roles vary meaning viewing important and restricted information may not be applicable to all users. Field masking allows the user role to be configured to specific permissions level. For instance, when purchasing a product, a sales executive may use a customer’s credit card or social security number and field masking may provide protection from that scenario.
- Compliance with Regulations: There are laws of privacy that encompass many fields like GDPR (General Data Protection Regulation) and also PCI-DSS (Payment Card Industry Data Security Standard) and HIPAA (Health Insurance Portability and Accountability Act). Field masking finds its effectiveness in fulfilling these requirements by masking important information only for people who are not permitted to see it.
- Preventing Internal Threats: Preventing Internal Threats: Despite the fact that hacking is the most talked about type of security breach, companies remain vulnerable even in their own households where an employee or a contractor may maliciously obtain data that is meant to be restricted. By use of field masking, the threat of such policies is greatly diminished, because good practice dictates that such fields should never be loaded for users even if they are in the system.
How to Implement Field Masking in vTiger CRM
vTiger CRM allows quite a good level of customization for users, roles and their visibility including the level of access to specific fields. Even though vTiger does not have a feature for field masking, the same can be achieved through a combination of custom fields, roles and modules. This is how you can generally implement field masking in vTiger:
1. Identify Sensitive Fields:
This is the first step in using field masking, then point globalization in vTiger CRM. This step may include:
- Personally identifiable information (e.g., social security numbers, addresses)
- Credit card and bank accounts
- Health related or confidential business information
2. Use Custom Fields for Masking:
- Users in vTiger CRM have the ability to create custom fields and apply field masking on a manual basis. The following are some methods to mask data in custom fields: First, for fields such as mobile numbers, a custom field can be created that will contain only a part of it, say the last few digits for instance.
- Encrypted Fields – If such fields are exposed then they too will be unreadable as such sensitive fields could be encrypted and without the correct decryption keys they would remain that way as long as no one has the keys.
3. Role-Based Permissions:
- Robust role-based access control is built into vTiger CRM which allows the users to perform roles keep varying permissions. To mask sensitive fields, you need to do the following: Set permissions such that they restrict certain users from viewing sensitive fields.
- Those roles which are authorized for that (for example the Role could be system administrators or finance officers). Only added those roles which are authorized to it, that being, masked or encrypted fields.
4. Use Extensions or Custom Modules:
In addition, here the modules are also okay and they are quite a number including vTiger extensions and third party modules that can provide more advanced field masking and even more encryption. You may use these together with your CRM system so that the tasks of field masking can be automated as well as data security tightened up.
Some popular modules or extensions to look into:
- SecuritySuite: An additional tool that allows restricting records and fields in vTiger.
- Custom Fields Module: Intended for creation of encrypted fields whereby various masking techniques may be applicable.
5. Regular Audits and Monitoring:
After implementation of field masking, regular audits should be done in order to check whether the requirements in regard to the protection of the sensitive information are met. You should also supervise user privileges by reviewing user access logs to restrict any unapproved access of masked or encrypted fields.
Best Practices for Field Masking in vTiger CRM:
- Limit Access Based on Need-to-Know: The access need of users to the masked fields must be strictly based on the principle of least privilege. Access to such fields must not be allowed if not required to perform a job duty.
- Monitor and Review Access: Carry periodic review of roles and permissions in the organization to reaffirm that the users have the right level of access, which is appropriate and that information is kept secure.
- Combine with Other Security Measures: Field masking should never be viewed as a stand alone feature. It should be used in combination with appropriate strong password policy controls that include two-factor authentication (2FA), data encryption and scheduled backups.
- User Training: Have your users understand the need for field masking and the security laws guiding sensitive data. This will reduce the chances of exposing the data to accidental leakage.
Conclusion:
vTiger CRM is a valuable application and could mostly contain sensitive data. Without field masking, the CRM can be a threat to the privacy of the customers. Field masking serves the purpose of obscuring fields which require privacy across the organization, and indeed this is possible when you apply custom fields, role-based permissions, or third party extensions.
If you’re not a proponent of waiting for a breach to happen, I suggest securing your CRM at this moment using the recent advance in technology, field masking.
Hope you found this blog useful.
We would be happy to assist you.
Please contact us on info@crmtiger.com if you needed further help from us.
Let us know if you need more information on this


Leave a Reply